Introduction
There are several good guides on the internet about upgrading your Active Directory Forest, Domains and Domain Controllers to Windows Server 2012 R2. I’d like to give you my strategy on this subject. It’s not wrong to add new Domain Controllers to your 2003/2008 domain, transfer the FSMO roles and demote the 2003/2008 DC’s, it’s the easy way but also prone to service interruption because you didn’t assess, plan and test before deployment. So, it’s possible to add some more steps to the process to smoothen things out and mitigate those risks.
In this scenario I’m going to assume that you replace your existing Domain Controllers without reusing hostnames and IP addresses.
Pre-migration
Test Your Backup
- Perform and test an actual forest recovery, simulate worst case scenario.. Test your backup in a separate isolated environment.
- After a successful forest recovery, test if the schema update works.
- Optional: add a 2012 R2 Domain Controller to the recovery environment to test successful dcpromo.
- Document your forest recovery scenario, have a valid and working disaster-recovery procedure in place.
Test Health of Active Directory
- Use DCDiag, FRSdiag, AD Replication Tool, to check for health issue’s, solve them first.
- Test DNS functionality.
- Update your existing DC’s to latest patch levels.
- Optional: leverage Microsoft ADRaaS (RAP as a Service)
Create Active Directory Inventory
- Document Forest and Domain architecture
- Document the replication topology
- Document DC’s: OS versions, service packs
- Document roles: FSMO, GC, DNS, DHCP, IAS etc.
- Document security settings: GPO, local policy, firewall
- Document other AD/DC specific changes: LDAP policies, dsHeuristics, SMB Signing, LM settings
Identify Risks
- Identify (legacy) applications that have dependency to Active Directory, the more you know the better.
- Create an inventory of all the applications that you have identified in the first step.
- Contact your software vendors to verify if Windows Server 2012 R2 DC’s are supported if they have AD dependency (FFL/DFL 2012 R2)
- In case you have physical DC’s (still recommended by Microsoft PFE’s) check hardware compatibility with 2012 R2.
- Check if any tooling used by your organization is compatible with 2012 R2 DC’s (Monitoring, Anti-Virus, Patch Management, Other Agents)
- Assess the Exchange Support Matrix and Lync support for AD see the supported Active Directory environments.
- Review KB944043 and KB2548145 and install if required.
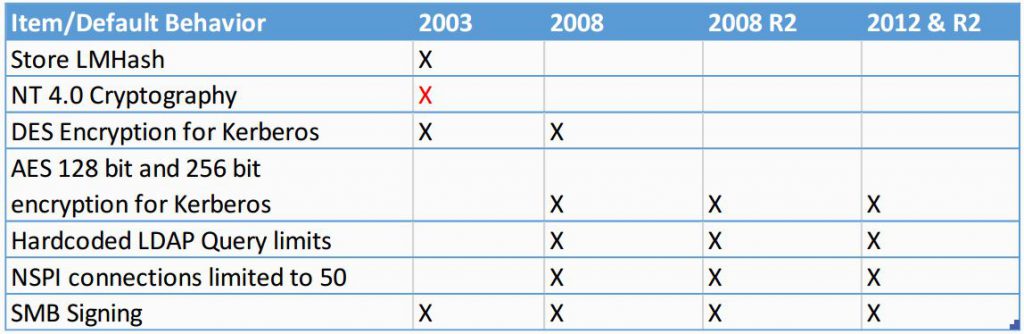
- Identify DES enabled accounts, they won’t work because DES encryption for Kerberos is disabled by default. Any keytab files maybe?
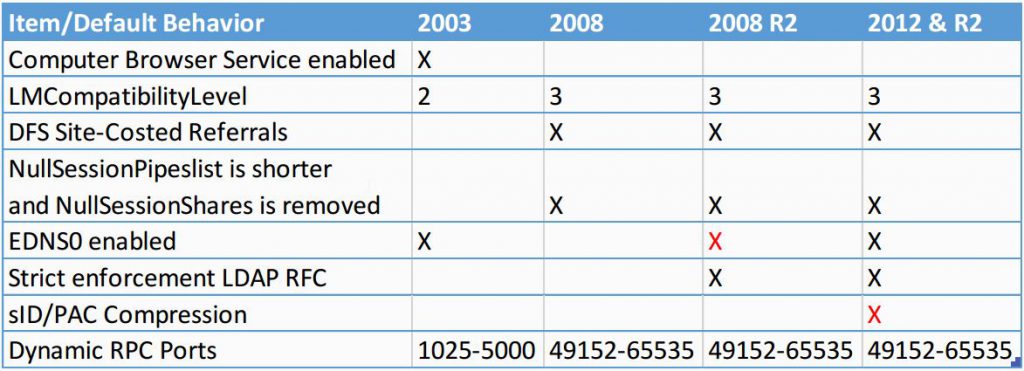
- Check compatibility:
Evaluate New Features
- Default Domain and DC policy differences.
- Schema version is updated from 30/31 (2003/2003 R2) 44/47 (2008/2008 R2)
- Powershell 3.o, Administrative Center, AD Recycle Bin, FGPP (PSO), NextGen Hypervisor, Snapshot Safeguard, DC Cloning, (g)MSA, DAC, FRS to DFSR.
- New policy features like User Account Control, Advanced Firewall, Advanced Auditing, additional user rights, KDC policies.
Plan
- Upgrade excisting DC’s or install and reuse same hostname and IP address or deploy additional 2012 R2 DC’s. What do you choose?
- Use Default Domain Controller Policy, create new GPO’s if you need to change settings, do not alter the Default Domain Controller Policy.
- Use and implement baseline policies from Microsoft SCM 3.o (Security Compliance Manager).
- Create WMI filters at OS level to apply new baseline policies.
- Create and use the “hidden site” feature before deploying the first 2012 R2 DC to your domain. Hide them from general use, no SRV record registration. Dynamic clients use DCLocator, DCLocator use SRV DNS records, use sites and GPO to control this feature. This is an important step!
- Use Microsoft PortQry to test if required Active Directory ports are functional (trust relationships, firewalls)
- If possible, consider the use of Core edition of Windows Server.
Migration Start
Deployment of First 2012 R2 DC
- Execute adprep /forestprep /domainprep and /rodcprep as a separate step, not through the Server Manager wizard. Check adprep log.
- Promote first Windows Server 2012 R2 domain controller to domain, this DC is added to your “hidden site” as desscribed earlier. Check dcpromo log.
Test
- Now that your first 2012 R2 DC is in place you can test against it. Take your findings you’ve gathered from the pre-migration section.
- Any applications that have AD dependency, test them now. LDAP connectivity, Kerberos authentication, performance.
- Now that you are comfortable with a live 2012 R2 DC deploy more 2012 R2 DC’s as needed. Add them to your special “hidden site”.
Make the Switch!
- Make the switch, remove the 2012 R2 DC’s from the “hidden site”, add your 2003/2008 to the “hidden site”, we reverse the process. This step requires you to reboot all the DC’s, please one at a time.
- Make sure the 2012 R2 have registered the SRV records in DNS and the SRV of the old DC’s have been removed. If all is correctly setup this process is automated.
- Take your time because you are changing group membership and applied GPO’s. Also, take some coffee at this moment 😉
- Perform tests like DCdiag /test:dns and repadmin /replsum
- Optional: in case anything went wrong, business is down, CEO stands at your desk with chainsaw, perform a roll-back. That’s the beauty of this approach. It offers you an actual roll-back to get things back to the way they were. Revert the process.
Hardcoded References
- Now that your old DC’s are isolated, search for hardcoded references to your 2003/2008 DC’s.
- Analyze logfiles: DNS debug logging, Netlogon debug logging, netmon, ETW tracing, eventlog. Almost everything in logging is hardcoded from now on.
Post-Migration
Migrate Clients
- Migrate clients and other network services (DHCP) to the new DNS servers IP addresses, migrate other systems to use the new DC’s (Kerberos, Keytab)
- Migrate remaining services that eventually popped-up.
Shutdown old DC’s
- Now it’s time to shutdown your old 2003/2008 DC’s, let them be offline for at least a week, 2 weeks recommended. If anything happens bring them back online and troubleshoot.
- After this period bring your old DC’s back online and perform a demote. Yay!
Migrate to new features
- Raise Forest and Domain functional levels to 2012 R2
- Cleanup SYSVOL, after cleanup migrate FRS to DFS-R
- Enable recycle bin
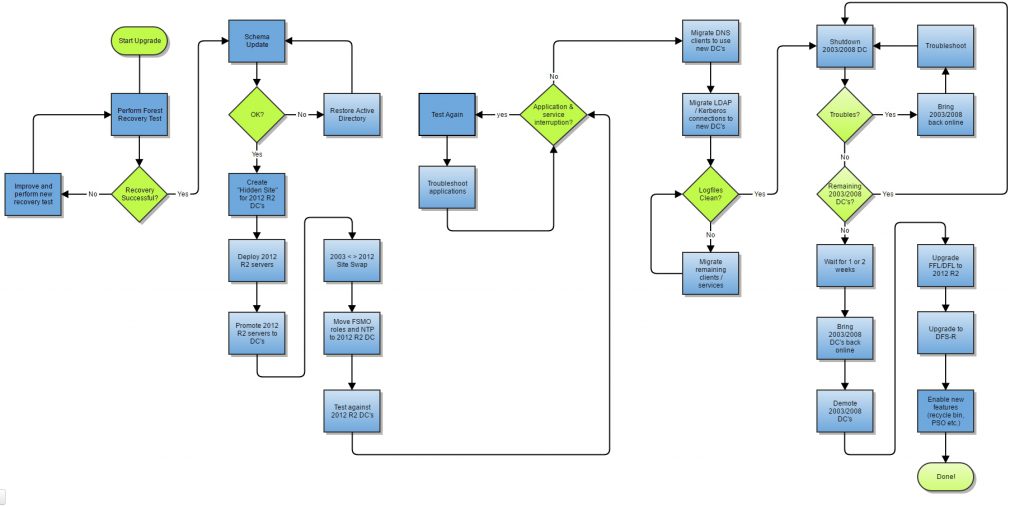
Flowchart
May your upgrade be successful!
References
Upgrade Domain Controllers to Windows Server 2012
http://technet.microsoft.com/en-us/library/hh994618.aspx
Microsoft Virtual Academy – 2012 sessions
https://www.microsoftvirtualacademy.com/colleges/WindowsServer2012
Server 2012 Requirements
http://technet.microsoft.com/library/jj134246#BKMK_sysreq
GlennL Blog on safe upgrade
http://blogs.technet.com/b/glennl/archive/2010/08/13/minimizing-risk-during-ad-upgrades.aspx
Windows Server 2012: Changes Made by Adprep.exe
http://technet.microsoft.com/en-us/library/hh994609
Install and deploy 2012
http://technet.microsoft.com/en-us/library/hh831620
Forest and Domain Functional Levels
http://technet.microsoft.com/en-us/library/understanding-active-directory-functional-levels(v=WS.10).aspx
Dynamic Access Control
http://technet.microsoft.com/en-us/library/hh831717.aspx
What’s new in 2012 Certificate Services
http://technet.microsoft.com/library/hh831373.aspx
What’s new in 2008/R2 Auditing
http://technet.microsoft.com/en-us/library/dd560628(v=WS.10).aspx
http://technet.microsoft.com/en-us/video/windows-server-2008-active-directory-auditing-enhancements.aspx
Authentication Mechanism Assurance
http://technet.microsoft.com/en-us/library/dd378897(v=WS.10).aspx
New Kerberos Features
http://technet.microsoft.com/en-us/library/hh831747.aspx
LMCompatibilityLevel = 3
https://support.microsoft.com/en-us/kb/982734
https://support.microsoft.com/en-us/kb/889030
DES Encryption Disabled
https://support.microsoft.com/en-us/kb/977321
https://support.microsoft.com/en-us/kb/978055
AES Encryption Enabled
https://support.microsoft.com/en-us/kb/2768494
https://support.microsoft.com/en-us/kb/975616
Lan Manager Hash Disabled
https://support.microsoft.com/en-us/kb/299656
https://support.microsoft.com/en-us/kb/946405
SMB Signing Enabled
https://support.microsoft.com/en-us/kb/887429
https://support.microsoft.com/en-us/kb/823659
NT4 crypto Disabled
https://support.microsoft.com/en-us/kb/942564
LDAPS NLB Issue
https://support.microsoft.com/en-us/kb/2282241
https://support.microsoft.com/en-us/kb/2275950
LDAP RFC2696 Section 3 enforced
https://support.microsoft.com/en-us/kb/2468316
https://support.microsoft.com/en-us/kb/977180
http://www.ietf.org/rfc/rfc2696.txt
LDAP Query Policy modified from defaults
https://support.microsoft.com/en-us/kb/2009267
https://msdn.microsoft.com/en-us/enus/library/ms675656(VS.85).aspx
OCS 2007R2 schema conflict with 2008R2 AD forestprep
https://support.microsoft.com/en-us/kb/982020
Windows Server 2008 R2 NullSessionPipes list is shorter and NullSessionShares
https://technet.microsoft.com/en-us/library/dd162275.aspx
https://msdn.microsoft.com/en-us/library/aa365590(VS.85).aspx